iOS kernel exploitation archaeology (34th Chaos Communication Congress)
On December 27th 2017 I presented at the 34th Chaos Communication Congress (34C3) a talk on the technical details and the process of reverse engineering and re-implementation of the evasi0n7 jailbreak's main kernel exploit, titled "iOS kernel exploitation archaeology". Actually, I gave the same talk at the WarCon private event earlier in 2017 (June), but since there were no proceedings or slides published there, I thought it would be a good talk for 34C3! Both events, 34C3 and WarCon, were very well organized, but also very different both in content and of course size. Many thanks to the organizers and volunteers of both these awesome European conferences!
Examining the value of SafetyNet Attestation as an Application Integrity Security Control
Google promotes the SafetyNet Attestation API as a tool to query and assess the integrity status of an Android device. The official documentation, leaves no doubt that the main purpose of the SafetyNet Attestation API is to provide device integrity information to the server counterpart of mobile applications. The server counterpart may choose to limit the functionalities available to an app, if it's running on a device with compromised integrity protections. However, in the past year CENSUS has performed a number of assessments to mobile apps where SafetyNet was also used as an application integrity security check. Furthermore, best practices documents such as ENISA's "Smartphone Secure Development Guidelines" document of December 2016, clearly propose the use of SafetyNet as a measure to check an app's integrity status (see page 23).
To the best of our knowledge, Google has not publicly released any detailed official documentation or recommended the use of the SafetyNet Attestation API for application integrity purposes.
An introduction to the LightBulb Framework
This blog post serves as a followup to my summer B-Sides Athens 2017 talk entitled “Lightbulb framework – shedding light on the dark side of WAFs and Filters”.
shadow v2 public release
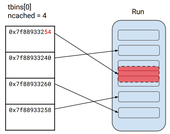
About four months ago (April 2017), Vasilis Tsaousoglou and myself presented our work on exploiting Android's libc allocator at the 2017 INFILTRATE conference (Miami, Florida). Since version 5.0, Android has adopted the jemalloc allocator as its default libc malloc(3) implementation. For our talk we extended our previously released jemalloc heap exploration and exploitation tool called 'shadow' to support Android (both ARM32 and ARM64), and demonstrated its use on understanding the impact of libc heap corruption vulnerabilities. We also presented new jemalloc/Android-specific exploitation techniques for double free and arbitrary free vulnerabilities.